Secured VLAN
Enterprise-Grade Network Segmentation & Security Best Practices
View on GitHubSecured VLAN: Enterprise-Grade Network Segmentation & Security
1. Project Overview & Core Objectives
Secured VLAN is a comprehensive blueprint for building a secure, scalable, and auditable enterprise network. This project demonstrates how to implement robust network segmentation, enforce least-privilege access, and centralize security controls using VLANs, ACLs, and firewalls. Designed for real-world deployment, it addresses challenges such as blurred internal-external boundaries, remote access, and evolving security threats.
Key Objectives:
- Strict departmental isolation with VLANs
- Enforced access policies using ACLs and firewalls
- Centralized logging for compliance and future AI-driven analysis
- High availability and resilience across all network layers
- Scalable, modular design for future expansion
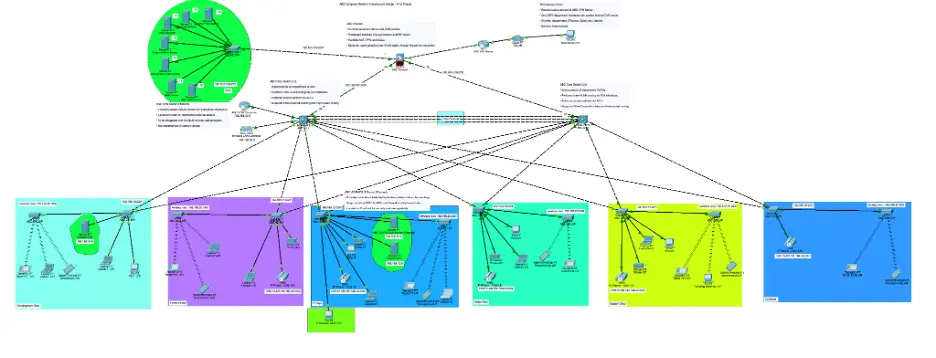
Figure 1: Example of a three-tier enterprise network topology with VLAN segmentation and DMZ.
2. Enterprise Network Security Architecture
2.1 Three-Tier Segmentation Model
The network adopts a classic three-tier architecture to maximize both performance and security:
- Core Layer: High-speed routing, OSPF dynamic routing, and HSRP redundancy.
- Distribution Layer: Dedicated switches for each department, enforcing VLAN boundaries and ACLs.
- Access Layer: End device connections with port security and dynamic VLAN assignment.
This layered approach enables granular control over inter-departmental traffic and supports scalable growth. Each layer is designed to be independently resilient, supporting both redundancy and rapid failover.
2.2 VLAN Design & Departmental Isolation
Each department is assigned a dedicated VLAN, strictly separating traffic and minimizing attack surfaces. Special-purpose VLANs are provisioned for wireless, voice, and DMZ services. This structure enables:
- Clean traffic segmentation
- Enforceable inter-department restrictions via ACLs
- Logical mapping of user identity to network access
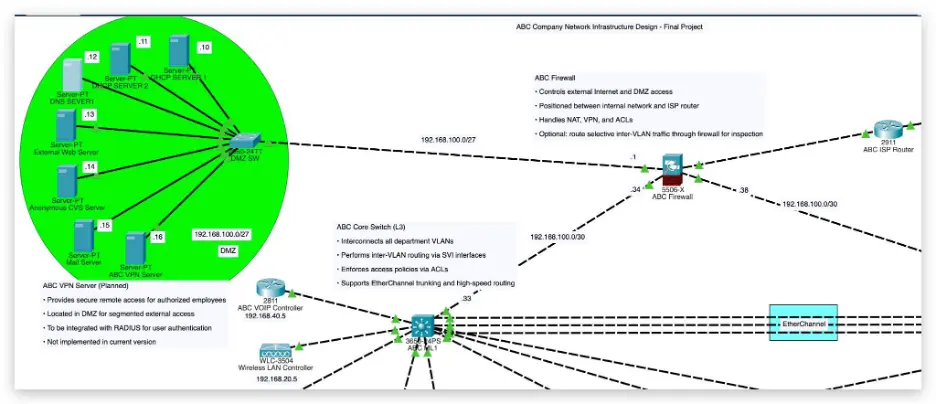
Figure 2: VLAN segmentation ensures each department’s traffic is isolated, reducing lateral movement risk.
| VLAN ID | Subnet | Department | Access Scope |
|---|---|---|---|
| 1001 | 192.168.10.0/24 | Development | CVS Server, Internet |
| 1002 | 192.168.13.0/24 | Sales | Web access only |
| 1003 | 192.168.12.0/24 | IT | Full network access |
| 1004 | 192.168.15.0/24 | Cafeteria | Guest Wi-Fi only |
| 1005 | 192.168.14.0/24 | Support | Shared internal tools |
| 1006 | 192.168.11.0/24 | Finance | Email, limited internal |
| 20 | 192.168.20.0/24 | Wireless | Dynamic via WLC |
| 40 | 192.168.40.0/24 | VoIP | Internal phone routing |
| 100 | 192.168.100.0/27 | DMZ | Public services |
Design Philosophy:
- One VLAN per department, mirroring business boundaries
- ACLs enforce a default-deny policy; only explicitly allowed traffic is permitted
- Special VLANs for wireless, voice, and DMZ ensure further segmentation
2.3 DMZ and Public Service Protection
All public-facing servers are deployed in the DMZ (VLAN 100), with access tightly controlled by the firewall. Only necessary ports (e.g., 80/443 for web, VPN, mail) are open to the Internet. Internal access to the DMZ requires explicit ACL permissions. Cloudflare WAF can be integrated to shield public services and mask real IPs.
3. Access Control & Policy Enforcement
3.1 ACL-Based Role Enforcement
Access Control Lists (ACLs) are deployed on both the firewall and Layer 3 switch interfaces to strictly control inter-VLAN and external access. The network follows a default-deny policy: all cross-VLAN traffic is blocked unless explicitly allowed.
Example: Allow VPN users to access only the CVS server
access-list VPN_SPLIT extended permit tcp any host 192.168.10.9 eq 443
access-list VPN_SPLIT extended deny ip any 192.168.11.0 255.255.255.0
access-list VPN_SPLIT extended deny ip any 192.168.13.0 255.255.255.0
Example: Finance VLAN blocked from Dev and IT
ip access-list extended BLOCK-FINANCE
deny ip 192.168.11.0 0.0.0.255 192.168.10.0 0.0.0.255
deny ip 192.168.11.0 0.0.0.255 192.168.12.0 0.0.0.255
permit ip any any
Where ACLs Are Applied:
- ASA firewall: for VPN, DMZ, and inter-zone traffic
- L3 SVI interfaces: for internal VLAN segmentation enforcement
3.2 NAT and Public Service Exposure
All public-facing services (CVS, VPN, mail) are hosted in the DMZ and require NAT. Only necessary ports are exposed, and the real IPs are hidden behind the firewall and Cloudflare.
Example: Port-forward public HTTPS to internal CVS
object network obj_CVS
host 192.168.10.9
nat (inside,outside) static interface service tcp 443 443
4. Key Technology Stack & Implementation
4.1 Core Routing & High Availability
To ensure both performance and resilience, the network leverages industry-standard protocols and redundancy mechanisms:
- OSPF (Open Shortest Path First): Dynamic routing and rapid failover
- HSRP (Hot Standby Router Protocol): Gateway redundancy
- EtherChannel: Link aggregation for throughput and redundancy
Sample Configuration:
interface Vlan10
ip address 192.168.10.2 255.255.255.0
standby 1 ip 192.168.10.1
standby 1 priority 120
standby 1 preempt
interface range GigabitEthernet1/0/1 - 4
channel-group 1 mode active
These mechanisms guarantee high availability for critical business operations. All key VLANs (Dev, IT, Finance) use HSRP, ensuring no gateway disruption during switch maintenance or failure. EtherChannel bundles multiple links for both performance and redundancy.
4.2 Firewall & DMZ Protection
A Cisco ASA firewall acts as the central policy enforcement point for all cross-VLAN, DMZ, and external traffic. The DMZ (Demilitarized Zone) hosts public-facing services such as web, mail, and VPN, protected by strict ACLs and NAT.
- Firewall Roles:
- Enforce access policies between internal, DMZ, and external zones
- Handle NAT for public services, exposing only necessary ports
- Log all significant network events for compliance and auditing
Sample ASA Logging Configuration:
logging enable
logging trap informational
logging host inside-2 192.168.12.100
4.3 Wireless & VPN Security
Wireless access is tightly controlled using a centralized Wireless LAN Controller (WLC):
- Staff and guest SSIDs mapped to separate VLANs
- Port security and dynamic VLAN assignment prevent unauthorized access
- VPN gateway in the DMZ allows only authorized users (e.g., Development team) to access internal resources, protected by multi-factor authentication (MFA) and ACLs
SSID to VLAN Mapping Table:
| SSID | VLAN | User Type | Access Scope |
|---|---|---|---|
| ABC-Staff | VLAN 20 | Employees | Per-role, internal |
| ABC-Guest | VLAN 1004 | Visitors | Internet-only |
| VoIP-AP | VLAN 40 | Phones | Internal VoIP only |
Wireless Security Highlights:
- Staff and guest traffic are fully isolated
- Future upgrades can include RADIUS-based identity assignment for even finer control
VPN Access Policy:
- Only specific users/groups are allowed
- Split tunneling restricts access to only necessary internal resources
- All login attempts and sessions are logged for auditing
5. Typical Attack Defense Scenarios
5.1 Lateral Movement & Ransomware Containment
A common attack vector in flat networks is lateral movement, where an attacker compromises one endpoint and attempts to access sensitive systems in other departments. With strict VLAN segmentation and ACLs, such movement is blocked by default. For example, if a Sales PC is compromised, ACLs prevent it from reaching the Finance VLAN or internal servers in the Development VLAN, containing the threat and reducing the blast radius.
5.2 DMZ Isolation Against External Threats
Public-facing services in the DMZ are isolated from the internal network. Even if a web server in the DMZ is breached, attackers cannot directly access internal resources due to firewall rules and ACLs. Only specific, tightly controlled flows (e.g., admin SSH from IT VLAN) are permitted, and all access is logged for auditability.
5.3 Wireless Guest Segregation
Guest Wi-Fi is mapped to a dedicated VLAN with Internet-only access. Guests cannot access internal resources, printers, or sensitive data, even if their device is compromised. This is enforced at both the WLC and firewall levels.
Summary: These scenarios demonstrate how layered segmentation, ACLs, and DMZ design provide robust defense-in-depth, making the network resilient against both external and internal threats.
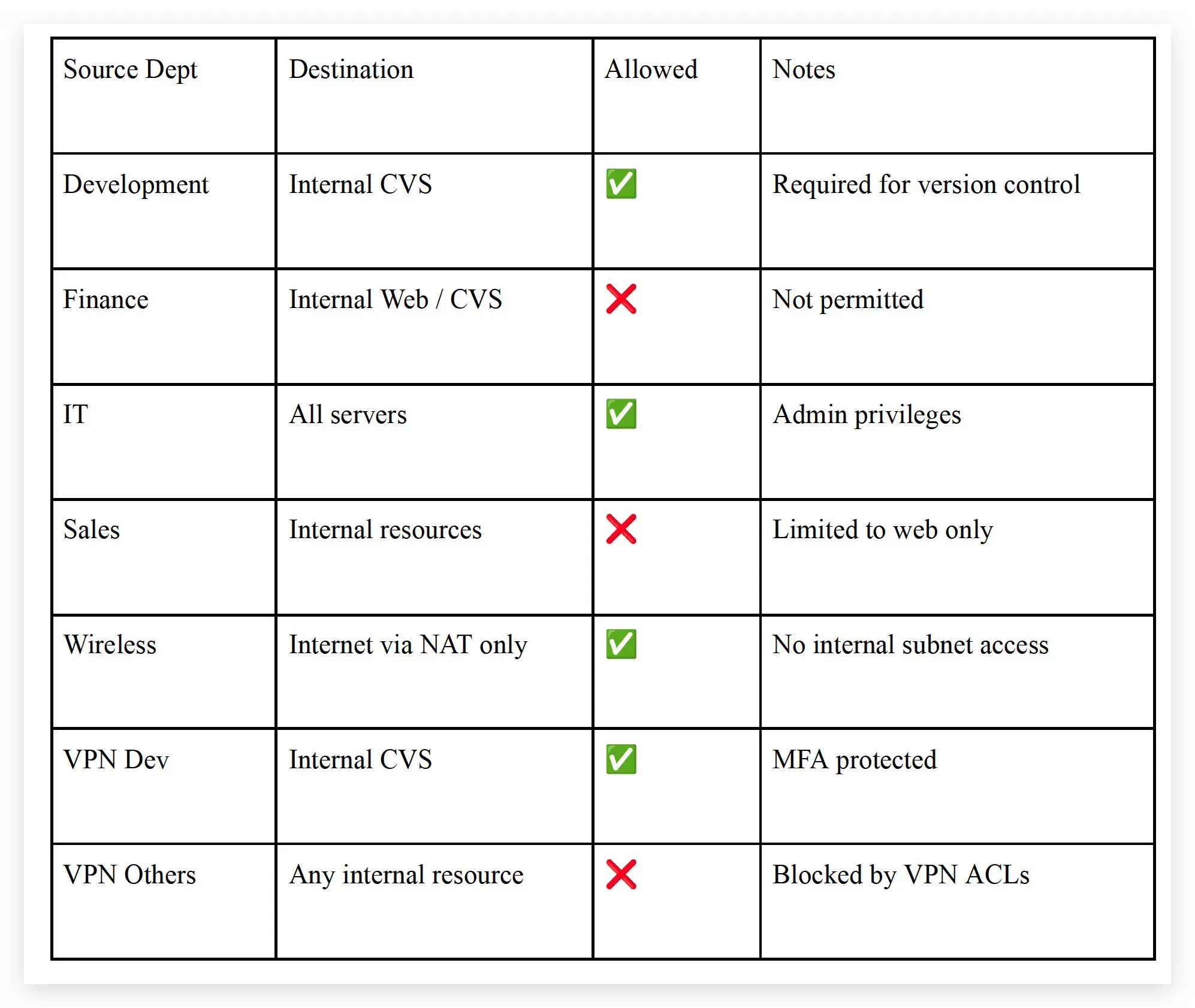
Figure 3: VLAN and ACLs block lateral movement, containing threats to the compromised segment.
6. Logging, Monitoring & Future AI Integration
6.1 Centralized Logging & Visibility
All network devices forward logs to a centralized syslog server, enabling:
- Comprehensive visibility into access attempts, configuration changes, and security events
- Easy integration with SIEM or future AI-driven analysis tools for threat detection and incident response
Sample Log Events:
- %ASA-6-302013: Built outbound TCP connection for outside:203.0.113.2/443 to inside:192.168.10.9/443
- %ASA-6-106100: access-list INSIDE_ACCESS permitted tcp inside/192.168.11.33(54211) -> dmz/192.168.100.20(25)
- %HSRP-5-STATECHANGE: Vlan10 Active -> Speak
6.2 AI-Driven Analysis (Planned)
While not yet implemented, the architecture is designed for future AI-based log analysis. This will enable:
- Automated threat detection and incident summarization
- Behavioral profiling and anomaly detection
- Proactive security recommendations
- Real-time visualization and automated response
6.2.1 Planned AI Log Analysis Architecture
The future AI-driven log analysis system will consist of several key components:
- Log Ingestion: Collect logs from firewalls, switches, WLCs, VPN gateways, and servers via syslog or log shippers (e.g., Fluentd).
- Normalization: Parse and convert raw device logs (e.g., Cisco ASA, WLC, Linux syslog) into structured JSON for downstream processing.
- LLM-Based Summarization: Use large language models (LLMs) such as GPT or LLaMA to interpret, summarize, and classify log events, providing human-readable insights.
- Event Correlation: Automatically link related events (e.g., failed logins, ACL denials, VPN disconnects) into incident storylines for root cause analysis.
- Risk Scoring: Assign severity levels to events using heuristics and NLP, helping prioritize alerts.
- Dashboard Integration: Visualize trends, alerts, and summaries in a web dashboard (e.g., Node.js + ECharts or Grafana).
- Automated Response: In future iterations, the system could trigger automated actions (e.g., block IP, disable account) based on AI-detected threats, further reducing response time.

Figure 4: Planned AI-driven log analysis pipeline, from ingestion to visualization and response.
Example AI Processing Pipeline:
- Log Ingestion → 2. Normalization → 3. LLM Analysis → 4. Correlation → 5. Scoring → 6. Dashboard/Alerting/Response
Sample Use Case:
- Raw Log:
%ASA-6-106100: access-list INSIDE_ACCESS denied tcp 192.168.13.33(40412) -> 192.168.10.9(443) - AI Output:
{ "severity": "medium", "source_ip": "192.168.13.33", "target_ip": "192.168.10.9", "action": "Blocked", "summary": "A Sales department machine attempted to access the Development CVS Server, which is not allowed per policy." }
Potential Advanced Features:
- Behavioral Profiling: Track login locations, access frequency, and detect anomalies.
- Config Drift Detection: Compare device configs over time to spot unauthorized changes.
- CVE Matching: Map firewall/NAT/services to known vulnerabilities for proactive patching.
- Lateral Movement Detection: Identify scanning or suspicious access patterns across VLANs.
- Automated Reporting: Generate daily/weekly incident summaries for admins.
- Integration: Slack/Discord bots, email alerts, and live dashboards.
Note: All AI features are in the planning stage. The current system is fully functional with traditional logging and monitoring, and is designed to be AI-ready for future upgrades.
7. Engineering Deployment & Operations
7.1 Rollout and Change Management
A successful network security deployment requires careful planning and staged rollout. Recommended steps include:
- Lab Simulation: Use Cisco Packet Tracer or GNS3 to validate all configurations before production.
- Phased Deployment: Roll out VLANs, ACLs, and firewall rules in stages, starting with non-critical segments.
- Change Management: Document all changes, use version control for configs, and implement a formal approval process for production changes.
- Rollback Planning: Always have a tested rollback plan in case of unexpected issues.
7.2 Operations and Troubleshooting
- Monitoring: Continuously monitor logs and network health via dashboards and alerts.
- Incident Response: Establish clear procedures for responding to detected threats or outages.
- Regular Audits: Periodically review ACLs, VLAN assignments, and firewall rules to ensure they match business needs and compliance requirements.
- Common Issues:
- Misconfigured ACLs causing legitimate traffic to be blocked
- VLAN trunking mismatches between switches
- NAT or firewall rules accidentally exposing internal resources
Tip: Maintain a knowledge base of troubleshooting steps and lessons learned to accelerate future incident resolution.
8. Best Practices & Real-World Application
8.1 Role-Based Segmentation & Zero Trust
The network’s design enforces the principle of least privilege at every layer:
- Each department’s devices are isolated by default
- Inter-departmental access is only allowed when explicitly required and approved
- All access attempts are logged, supporting both security and compliance
8.2 High Availability & Resilience
Redundancy is built into every layer:
- HSRP ensures uninterrupted default gateways
- EtherChannel mitigates cable failure and boosts performance
- OSPF dynamically re-routes traffic in real time
- All failovers are logged, traceable, and explainable
8.3 Practical Use Cases & Reusability
This architecture is suitable for:
- Corporate campuses needing strict departmental segmentation
- Educational or research institutions with diverse user groups
- Manufacturing environments requiring secure separation of IoT and admin systems
- Training labs for security policy simulation and testing
All configurations are reproducible in Cisco Packet Tracer and can be adapted for real hardware deployments. The open-source repository includes full topology, configuration files, and templates for rapid deployment.
9. Conclusion & Future Directions
ABC Secured VLAN demonstrates that enterprise-grade network security is achievable with clear segmentation, strict access control, and centralized monitoring. The architecture is scalable, auditable, and ready for future enhancements such as AI-driven threat analysis. All configurations and templates are open source and reusable for real-world or educational deployments.
This blueprint stands ready for real-world deployment, evolution, and education.
🔐 Security is not a feature. It’s a posture.
📽️ Inspired By Two Outstanding Professors
👨🏫 Professor Talia Q — CIS-221 (Information Systems Security)
Professor Talia Q’s deep teaching and hands-on labs sparked the entire vision behind this project.
His network forensics labs, Kali Linux demonstrations, and real-world insights into layered defense strategies fundamentally shaped this work.
👨💻 Professor Samuel Okegbile — CIS-192 (Networking)
His comprehensive VLAN architecture lectures and 3+ hour walkthrough on secure hierarchical designs laid the foundation for this network’s structure.
📺 Design and Implementation of a Secure Company Network System
💡 With his guidance, I implemented: VLANs, ACLs, ASA Zones, WLC Wireless, DHCP, Inter-VLAN Routing, IP Phones, HSRP, NAT, EtherChannel, STP Guard, OSPF, SSH hardening — and more.
- For more on VLAN and network segmentation best practices, see Cisco’s VLAN Design Guide.
- Learn about Cloudflare’s WAF and Zero Trust solutions for DMZ and public service protection.
- Reference NIST SP 800-41 for firewall and ACL policy recommendations.
- Explore OWASP Top 10 for common web application threats relevant to DMZ design.
- For OSPF and routing protocol standards, see RFC 2328.
- For security logging and SIEM integration, review Elastic SIEM and Grafana.
Comments
This space is waiting for your voice.
Comments will be supported shortly. Stay connected for updates!
This section will display user comments from various platforms like X, Reddit, YouTube, and more. Comments will be curated for quality and relevance.
Have questions? Reach out through:
Want to see your comment featured? Mention us on X or tag us on Reddit.