Placed 2nd at BSides Vancouver 2025 Blue Team CTF – With Just ChatGPT and Stubbornness
How I placed 2nd solo at BSides Vancouver 2025 Blue Team CTF using only ChatGPT and Splunk: threat hunting, incident response, registry forensics, and AI-driven analysis.
Placed 2nd at BSides Vancouver 2025 Blue Team CTF – With Just ChatGPT and Stubbornness
Summary
I placed 2nd at the BSides Vancouver 2025 Blue Team CTF using nothing but ChatGPT and sheer persistence. This post covers how I tackled the competition with no team, no fancy toolkits, and a whole lot of stubborn curiosity. Here’s how it went.
1. About the Event: Blue Team CTF @ BSides Vancouver

BSides Vancouver is a respected community-driven infosec conference, and this year they added a Blue Team Capture The Flag (CTF) challenge to the agenda.

Unlike typical Red Team CTFs which focus on offensive tactics, the Blue Team CTF simulates a real-world incident response scenario:
- Analyze logs (mostly Splunk)
- Identify adversarial behavior
- Trace attacker techniques
- Extract IOC (Indicators of Compromise)
- Answer forensic-style questions in a time-limited scoreboard system
2. Tools & Methods: Just ChatGPT and Splunk
I didn’t go in with a team. I relied entirely on:
- ChatGPT-4: For crafting Splunk search queries, interpreting log formats, and understanding registry artifacts or obscure malware behavior.
- Splunk Web: The CTF platform provided full access to log data via Splunk dashboards.
I prompted ChatGPT in real time, iterated searches fast, and debugged logic based on actual logs.
No prebuilt playbooks. No teammates. Just AI and willpower.
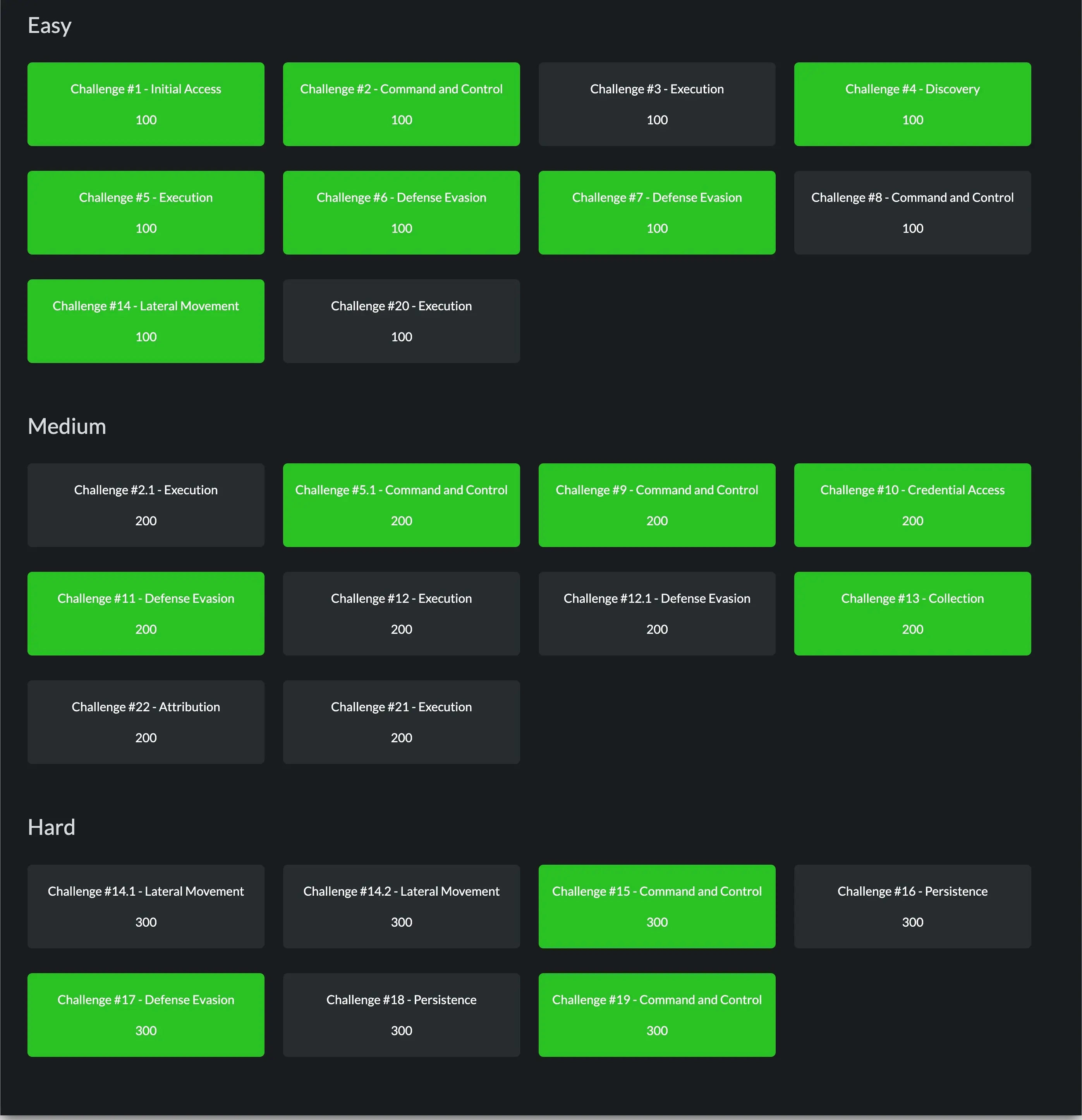
3. Highlights & Tough Spots
The challenge included:
- Threat Hunting: Tracing a persistent attacker across Windows Event Logs
- Registry Forensics: Identifying modified keys like
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options - Lateral Movement Detection: Logs from
psexec,wmiexec, andRemote Access.exe - Credential Access:
reg.exedumping SAM/SYSTEM/SECURITY toC:\Users\Public - RDP Artifacts: Inferring attacker source from volatile environment keys like
CLIENTNAME - Malware Attribution: Matching string artifacts with open-source malware on GitHub
Biggest blocker? Ambiguity. Some flags required pinpoint knowledge of Windows internals or parsing long PowerShell contexts.
Breakthrough? Letting ChatGPT reason over multiple queries, adjust search logic dynamically, and simulate hypothesis testing in real time.
4. Lessons & Takeaways
- AI is already a force multiplier for defensive analysts
- Prompt engineering > Tool fatigue: One clean query beats 100 unfocused clicks
- Persistence wins: Even when answers weren’t obvious, quick iteration pushed me through
- Blue Team CTFs teach critical real-world analysis far better than abstract theory
5. What’s Next: Building My Own AI Blue Team Sidekick
This competition validated my roadmap.
I’m now actively building a personal AI Security Assistant that:
- Integrates with SIEM/log platforms
- Has memory of incident chains
- Suggests queries, remediation actions
- Learns from previous investigations
This will be Phase 2 of my HarrisonSec project. Stay tuned.
6. Final Words + Media
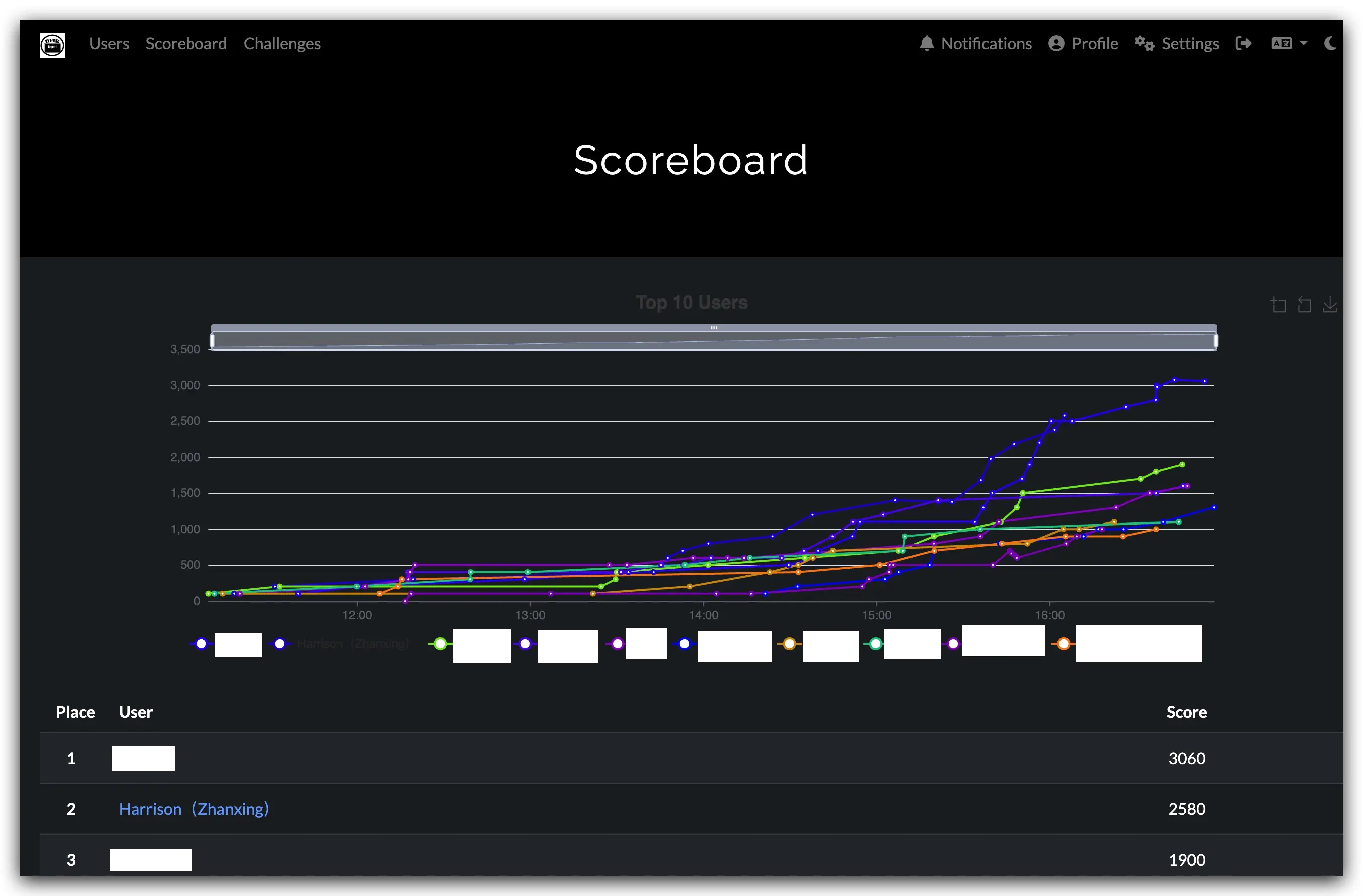
Thanks to BSides Vancouver organizers, volunteers, and competitors. Although I left a bit early, securing 2nd place solo (ahead of full teams) with just AI help feels rewarding.
If you found this useful:
- Follow me on LinkedIn
- Or X/Twitter @harrisonsec
- Visit: https://harrisonsec.com for my AI+Security lab and projects
#CTF #Blueteam #BSidesVancouver #AIForSecurity #ChatGPT #SIEM #Infosec #Splunk #AItools
Comments
This space is waiting for your voice.
Comments will be supported shortly. Stay connected for updates!
This section will display user comments from various platforms like X, Reddit, YouTube, and more. Comments will be curated for quality and relevance.
Have questions? Reach out through:
Want to see your comment featured? Mention us on X or tag us on Reddit.